It’s always a good idea to take precautions when storing your data online, but it’s especially important if you’re storing sensitive information like credit card numbers or social security numbers. Amazon S3 encryption is an easy way to secure your data in S3.
Amazon Web Services (AWS) provides the most reliable and scalable cloud computing platform in the world. The AWS Cloud includes Amazon Simple Storage Service (S3), which can store anything from photos, videos, music, and other digital content to virtual machines.
When it comes to safeguarding your data stored in Amazon S3, you’ll find a robust set of AWS S3 encryption options at your disposal. Amazon S3 encryption provides multiple layers of security to ensure the confidentiality and integrity of your data. One fundamental aspect is S3 encryption at rest, which allows you to encrypt your data while it resides in S3 storage, protecting it from unauthorized access or breaches. AWS S3 encryption options offer a variety of S3 encryption types, allowing you to choose the most suitable method based on your specific security requirements. With these comprehensive S3 encryption options, you can rest assured that your data remains shielded from potential threats, reinforcing the security of your cloud storage infrastructure.
What is Encryption?
Good question! Encryption is a method of protecting information by disguising it so that only authorized people can get through its security system. To get through this security system, one would need to have an “encryption key“. This can be thought of as a password – only the correct key will unlock all of your information.
The term encryption is derived from the Latin word encryptus, which means “to put something in a secret code for secrecy.“
Encryption is often used for protecting things like hacked account information, Social Security numbers, etc. There are far too many individual protective measures to list here, but encoding passwords and PINs (credit cards) come to mind.
If you ever use WiFi on your laptop or phone, encryption is what keeps your passwords and banking information under lock and key while you’re out in public – anyone attempting to “listen” in on your transmission would only get noise.
The goal of most encryption is to ensure that outside parties cannot access the information. This works with modern cryptography, which is why it’s often discussed in terms of protecting communication between computer users rather than just data storage.
Diverse Encryption Options for AWS S3 Data Security
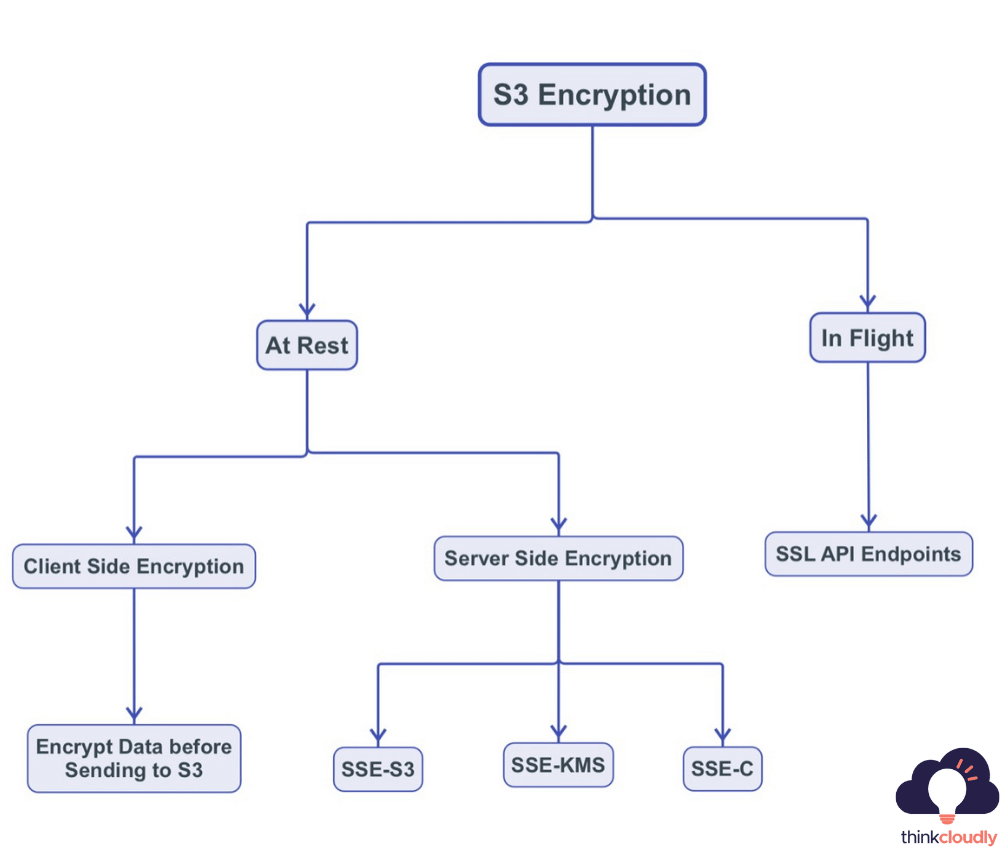
When it comes to securing data stored in Amazon S3, users can take advantage of a variety of encryption types and options provided by AWS. These S3 encryption types ensure that data remains confidential and protected from unauthorized access. AWS offers both server-side and client-side encryption options. Server-side encryption includes Amazon S3 managed keys (SSE-S3), AWS Key Management Service (SSE-KMS), and customer-provided keys (SSE-C). On the other hand, client-side encryption allows users to encrypt data locally before uploading it to S3, maintaining full control over encryption keys. With these AWS S3 encryption options, users can tailor their data protection strategies to their specific security requirements, bolstering the integrity and confidentiality of their stored information.
Boost your earning potential with AWS expertise. Explore our certified AWS Courses for a high-paying career
Encryption Methodologies
AWS S3 provides two different types of security for your data, Encryption in Transit and At-Rest.
Encryption in Flight
AWS S3 provides you with an HTTPS endpoint to work on all of your object storage needs. It’s always recommended that when handling data in flight, or sending it back and forth between clients (S3 included), encryption be enabled at every level possible including the client side via SSL certificates, for example, this will make sure no one can see what information was encrypted within their transmissions which are especially useful if hackers are trying to steal sensitive info off someone else’s computer while they’re using crypto without thinking about its security!
Encryption at Rest
Encryption at Rest can be divided into two categories: client-side encryption and server-side encryption. For all symmetric key encryption operations, AWS uses AES-256 with Galois Counter Mode (GCM) for both server-side and client-side encryption. GCM provides authenticated encryption by adding a unique tag to the ciphertext.
Types of S3 Encryption
Amazon Web Services (AWS) currently offers a wide range of data encryption solutions. Amazon Elastic Block Store (Amazon EBS) encryption choices are also available. In this blog, we will be discussing S3 Encryption.
What is S3 encryption, and how does it work?
Amazon offers a variety of data encryption options for information stored in Amazon S3. Is S3 secure? By default, data kept in an S3 bucket isn’t encrypted, but you may change the AWS S3 encryption parameters.
After answering the questions below, you should select an encryption technique:
- Who is encrypting and decrypting the data?
- Who is storing the secret key?
- Who is managing the secret key?
Let’s take a look at the various AWS encryption options for S3 objects in a bucket.
Build Your Career as a
AWS Solution Architect
- Live Projects
- Resume / Interview Preparation

Client-side encryption (CSE)
Client-side encryption (CSE) is an S3 feature that allows you to encrypt data client-side before uploading it to S3.
Once CSE has been enabled on your bucket, only the AWS account owner and the IAM users who have access to encrypted files through policies can see unencrypted versions of such files in their Amazon S3 buckets.
Instead of storing unencrypted data, Amazon S3 encrypts customer content as customers upload it. The keys used for encryption are also stored by Amazon, so that they know which encrypted file goes with which customer. The files themselves, however, remain unencrypted while sitting in the customers’ Amazon S3 buckets and within AWS storage systems. With CSE at rest, even if the data is stored unencrypted on disk, Amazon S3 encrypts it with a key that is then protected by block-level encryption.
Server-Side Encryption (SSE)
Server-Side Encryption is the basic form of data encryption. The AWS cloud encrypts all of the information on its servers. You send unencrypted data to AWS, and then it will be encrypted before it is stored in the cloud storage. When you want information from your account, Amazon reads it and decrypts any necessary material for you before delivering unencrypted data across the network to you as a consumer.
Amazon S3-managed keys (SSE-S3)
The S3-SSE-S3 approach is the most straightforward — AWS encrypts and decrypts the data you’ve selected. You can’t see or use this key directly to encrypt or decode the material. AES-256 is used as the encryption algorithm, which is an acronym for Advanced Encryption Standard. AES (Advanced Encryption Standard) is a symmetric block cipher with a 256-bit cryptographic key length. If you have complete faith in AWS, this S3 encryption method is appropriate for you.
AWS KMS (SSE-KMS)
The SSE-KMS encryption type is similar to the SSE-S3 approach, but it has some key differences. The AWS Key Management Service (KMS) is utilized to encrypt data on the Amazon server. The data key is maintained by AWS, while the customer master key (CMK) is handled by AWS KMS users. User control and an audit trail are advantages of using the SSE-KMS encryption methodology.
Customer provided encryption key (SSE-C)
The encryption keys are not stored on AWS S3-C with SSE-C because the customer supplied them. Each request to AWS regarding data encryption or decryption is handled by the given key. A user must guarantee that the keys are secure. The encrypting of data on the AWS server is done using S3. Only an HTTPS connection (not HTTP) may be used.
Let’s Set Up Amazon S3 Encryption
Now that you know to protect your data, it is time for encryption. Amazon S3 offers two methods of encrypting objects: setting an individual object’s level and allocating a bucket with one set method. If there are no specific requirements or rules on how these encumbered files should be protected then simply create them using only approved algorithms- this ensures increased security in case something was ever hacked!
SSE- S3 Encryption
- Sign in to your AWS Management Console and search for S3.
 2. Start with creating an S3 bucket.
2. Start with creating an S3 bucket.
You can follow the steps given in Creating S3 Bucket and Objects to create a bucket.
- Now you can open the bucket to add objects to it.
 4. In the S3 Bucket dashboard, Click on Upload and then on Add Files to add files in the bucket.
4. In the S3 Bucket dashboard, Click on Upload and then on Add Files to add files in the bucket.
 5. Select the file from your system and click on open.
5. Select the file from your system and click on open.
6. After selecting the file, now we will encrypt it. Click on Properties and scroll down to Server-side Encryption Settings.
7. Here, you need to select Specify an encryption key.
8. Now select Encryption Key Type as Amazon S3 Key(SSE-S3) to finally encrypt the file with a key managed by S3.
9. Click on Upload.
You have successfully uploaded your first encrypted file in S3 Bucket. To check the same you can open the same object in the bucket and check if the encryption is enabled or not
But encrypting every file you upload can be very time-consuming and it will be difficult to change settings for each. So, a better option will be to change the encryption settings of the whole S3 Bucket at once which will lead to every file being encrypted already while being uploaded.
Steps to encrypt Bucket using SSE-S3
- Open S3 Bucket and click on Properties.
 2. In Default Encryption, click on Edit.
2. In Default Encryption, click on Edit.
3. Select Server-side encryption as Enabled and Encryption key type as Amazon S3 key(SSE-S3) in Default encryption. Click on Save Changes.
 Congratulations, you have completed all configurations. Now all the files uploaded will have default S3 Key Enabled Encryption.
Congratulations, you have completed all configurations. Now all the files uploaded will have default S3 Key Enabled Encryption.
SSE-KMS Encryption
Now to enable SSE-KMS encryption you need to follow the same steps as above for SSE-S3 encryption but the only change you need to do is while choosing Server-side encryption settings.
- In Server-side encryption, you need to choose to Specify an encryption key.
- Next, in the Encryption key type choose the AWS Key Management Service key (SSE-KMS).
- Now in AWS KMS key finally choose AWS managed key (AWS/s3). Click on Upload.
To check the encryption settings done and Key Policy attached, in Properties of the specific object you can try accessing the AWS KMS key ARN.
Congratulations! You have successfully encrypted your object file using AWS SSE-KMS.
Conclusion:
Amazon S3 is a great option for those who have an environment with various applications that generate large amounts of data. The very reason to choose S3 over other storage options is not only because it can store huge volumes at much cheaper rates, but also because it’s durable and scalable as well as highly available. Data privacy and compliance are vital when it comes to data security, which can be achieved using multiple encryption methods offered by Amazon S3.
When you use the right type of encryption on your data stored in Amazon S3, you’ll never need to worry about any information being compromised again. To learn more about AWS solutions or how we can help you better understand these topics, check out our courses and blogs!















