AWS IAM, or Identity and Access Management, is an integral component of AWS, especially as it pertains to compliance and governance of your cloud resources. Although IAM might seem relatively simple and straightforward at first glance, it’s actually quite nuanced and multifaceted. This introductory guide provides an overview of what AWS IAM is, how it works, and how you can use it within your own organization to help manage your cloud environment effectively.
In addition to understanding the fundamental concepts of AWS IAM, it’s essential to highlight the resources available for further learning. If you’re looking to delve deeper into AWS IAM and gain a comprehensive understanding, consider enrolling in an AWS 101 course or AWS IAM training program. These courses provide in-depth insights into how AWS IAM works and offer hands-on experience to help you master identity and access management in the AWS ecosystem. Whether you’re a newcomer to IAM 101 or seeking to enhance your existing knowledge, these training opportunities can be invaluable in your journey to becoming an AWS IAM expert.
“AWS IAM Course: IAM 101 Essentials”
“IAM 101: Unlocking the Fundamentals of AWS Identity and Access Management Course. Delve into the core concepts of AWS IAM with our comprehensive course. Learn how to manage user identities, secure access to resources, and implement fine-grained permissions. This course is designed to provide a solid foundation in IAM, making it ideal for beginners and those looking to reinforce their understanding of identity and access management in the AWS cloud.”
AWS Security Best Practices
When it comes to managing access to your AWS resources, there are a few best practices you should always follow. Two-factor authentication for all accounts (not just administrative ones) is a great place to start. There are also several best practices that apply directly to security groups.
Whenever possible, use security groups rather than network ACLs to define what users can and cannot do on EC2 instances. The reason for this is that when you use security groups, they can span multiple availability zones and regions in addition to giving you a single global namespace—all with little or no performance overhead.
Security group rules should be as narrow as possible while still meeting your needs; avoid unnecessary rules so your AWS infrastructure has maximum flexibility in case of an emergency or during a migration/restructuring period.
Finally, review and regularly modify any outbound rules associated with each of your VPCs—especially if new instances are launched into them frequently; add new resources before removing old ones; avoid deleting any existing rules from active VPCs without considering their effects carefully beforehand.
Why do we need AWS IAM?
Being in charge of your company’s IT department can be a daunting task. With all of today’s data breaches, security has become more important than ever before. To prevent these instances from occurring and protect your company’s data, it is critical that you understand how to properly secure and manage access control within your environment. Thankfully, there are technologies like Amazon Web Services (AWS) that allow you to do so easily and securely.
Build Your Career as a
AWS Solution Architect
- Live Projects
- Resume / Interview Preparation

What is AWS IAM?
Despite security concerns, many businesses are moving to the cloud. To ensure a smooth transition to AWS, AWS administrators need to follow security best practices. Despite all the attention Cloud platforms receive, AWS IAM takes a meticulous approach to permissions and access control within your environments. The AWS IAM function allows you to control which users are allowed to access and use your resources to create a secure environment.
As a web service, AWS Identity and Access Management (IAM) manages customers’ access to AWS services and resources. With IAM, you can create and manage users and groups, and specify which AWS services they can access and what actions they can perform. You can also create roles to allow users to access resources without remembering individual passwords.
Boost your earning potential with AWS expertise. Explore our certified AWS Courses for a high-paying career
How Does AWS IAM Work?
IAM systems are designed to provide four key benefits:
- Authentication – Verifying the identity of a user.
- Authorization – determining what a user is allowed to do.
- Auditing – tracking user activity.
- Identity management – managing user identities and roles.
This means that only the right people should have access to computers, hardware, software apps, and any other IT resources and perform specific tasks.
The essential components of an IAM framework include :
- A database of users’ identities and access privileges,
- IAM tools for creating, monitoring, modifying, and deleting access privileges, and
- A system for auditing login and access history.
Ensure your IAM privileges are always up-to-date by keeping your role changes and user additions in check. Usually, this falls under the responsibility of your IT department or data management section.
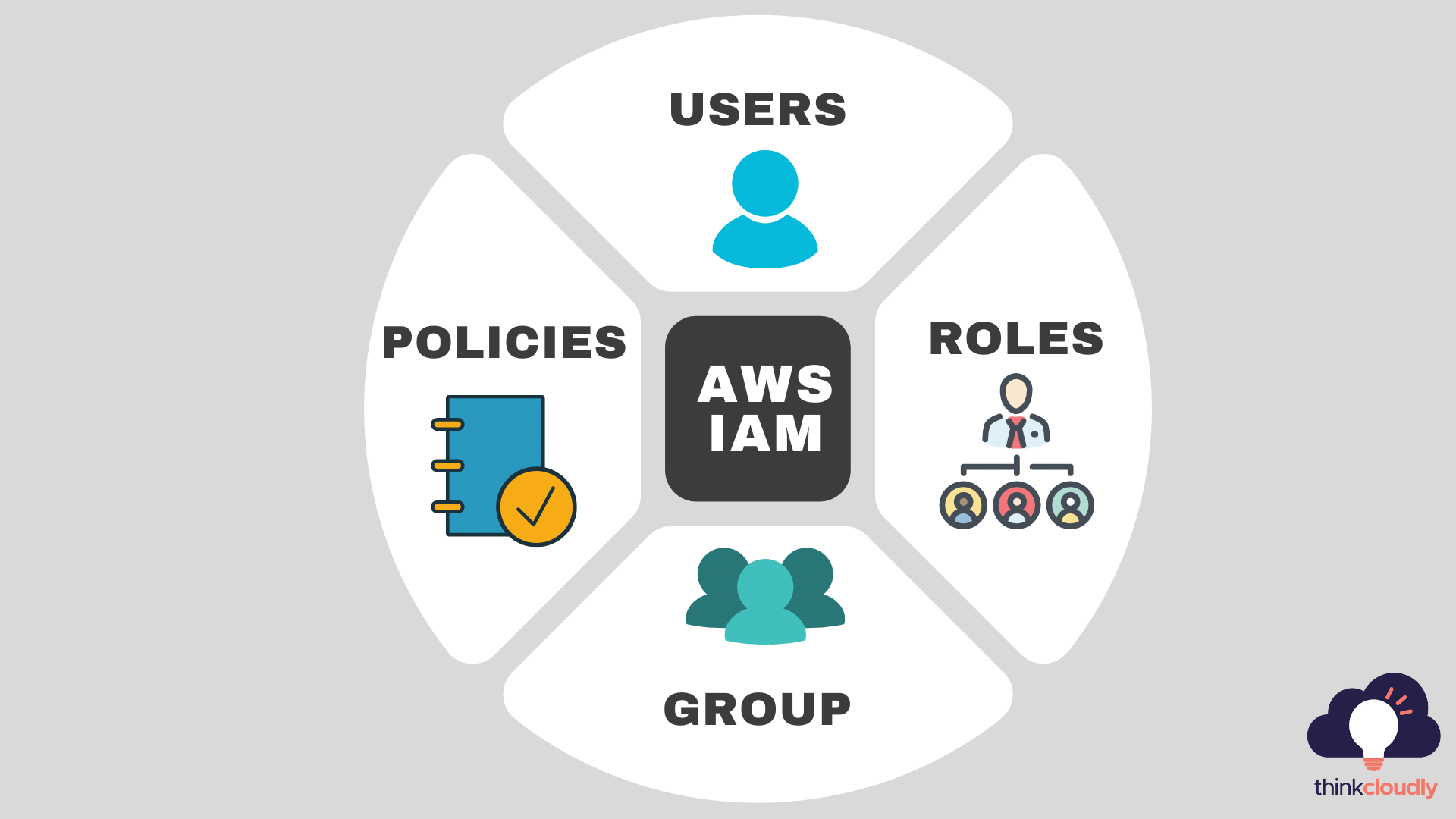
Components of AWS IAM
IAM users
IAM users are identities with credentials and permissions attached. A user could be an individual or an application. The IAM service lets you create a user name for every employee of your company so they can securely access AWS services. There can be one IAM user per AWS account. You can assign each IAM user to a group that has the permissions needed to perform particular tasks.
IAM Groups
IAM groups are collections of IAM users. IAM groups help specify permissions across multiple users so that any permissions granted to the group will also be given to the individual users in the group. Managing groups is relatively easy. You can create a group, add users to it, remove them from it, or change permissions in one place.
IAM policies
Configure the permissions that are needed for specific users, groups, and AWS resources. You can ensure that each user has their own unique set of permissions for each resource.
IAM roles
To access AWS resources, you need to define the permissions required for users and groups are the types of entities you create in your environment to grant security-related access to AWS services. IAM roles provide a more fine-grained capability for securing access to AWS resources.
Benefits of AWS IAM
1. Improved security – Your data is secure and safe when identity and access management is in place. By restricting access to your systems and data to only authorized users, you reduce the risk of a security breach.
2. Reduced cost – By implementing a network security solution you can gain control over your expenses and gain more insight into your data traffic, making it easier to identify what data is of the highest value and, therefore, most important to protect.
3. Improved efficiency – With more precise monitoring and control over your network, you can avoid disruptions and ensure that your systems are always available to your users, increasing efficiency and reducing costs.
4. IAM improves user experience- You only need one password to access all your systems with SSO. If you use biometrics or a smart card, you won’t need to remember any passwords at all!
5. IAM helps in compliance- With IAM, organizations can quickly implement IAM best practices that meet HIPAA and GDPR requirements.
AWS seems interesting to you. Explore our free resources, which will land you a job in your dream company.
- A blog over AWS IAM interview questions.
- A dictionary for AWS S3 interview questions.
- An article on AWS EC2 interview questions.
- An introductory guide for data ingestion in AWS.
- Program for AWS live projects training.
Don’t forget to register for free webinars to boost your knowledge.
Conclusion:
AWS Identity and Access Management (or IAM) is a service that enables you to securely control access to all of your AWS services and resources. It’s the foundation for security in Amazon Web Services, empowering users to create individual identities with specific permissions and policies, enabling multi-factor authentication, and tracking usage by identity or group across every AWS product line…and it’s free! To learn more about cloud technology, check out our blogs and training courses on our website today.